 I have always found difficult to operate properly with an Asterisk installation with Sip Trunk behind a Sonicwall router: the problem usually is the one-way communication router through one trunk, or other related issue.
I have always found difficult to operate properly with an Asterisk installation with Sip Trunk behind a Sonicwall router: the problem usually is the one-way communication router through one trunk, or other related issue.
To solve the issue there are the general rules I use.
1) Set the UDP timeout to 90 sec or more.
2) Do not use SIP transformations (Voip section) and modify the NAT behavior.
3) Eventually forward all the necessary ports to PBX in LAN.
In the next the images & notes of these configurations in Sonicwall TZ100.
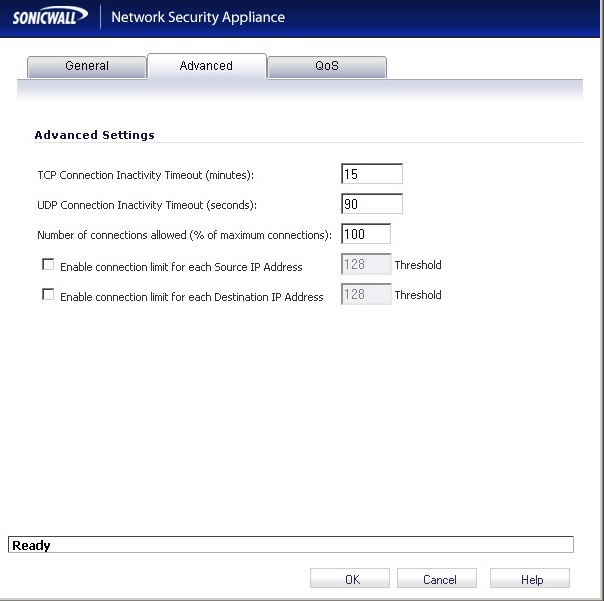
Firewall Settings –> Advanced
Modify the field “Default UDP Connections Timeout (seconds)”.
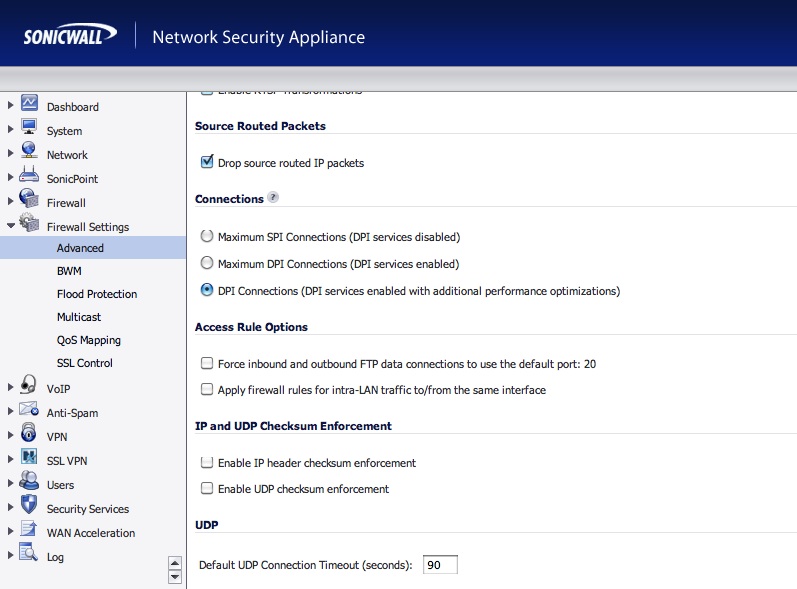
All the UDP connection related to new rules added to Sonicwall will have this value.
Firewall –> Access Rules –> LAN>WAN -> Edit
Modify the field “Default UDP Connections Timeout (seconds)” in the rule LAN->WAN.
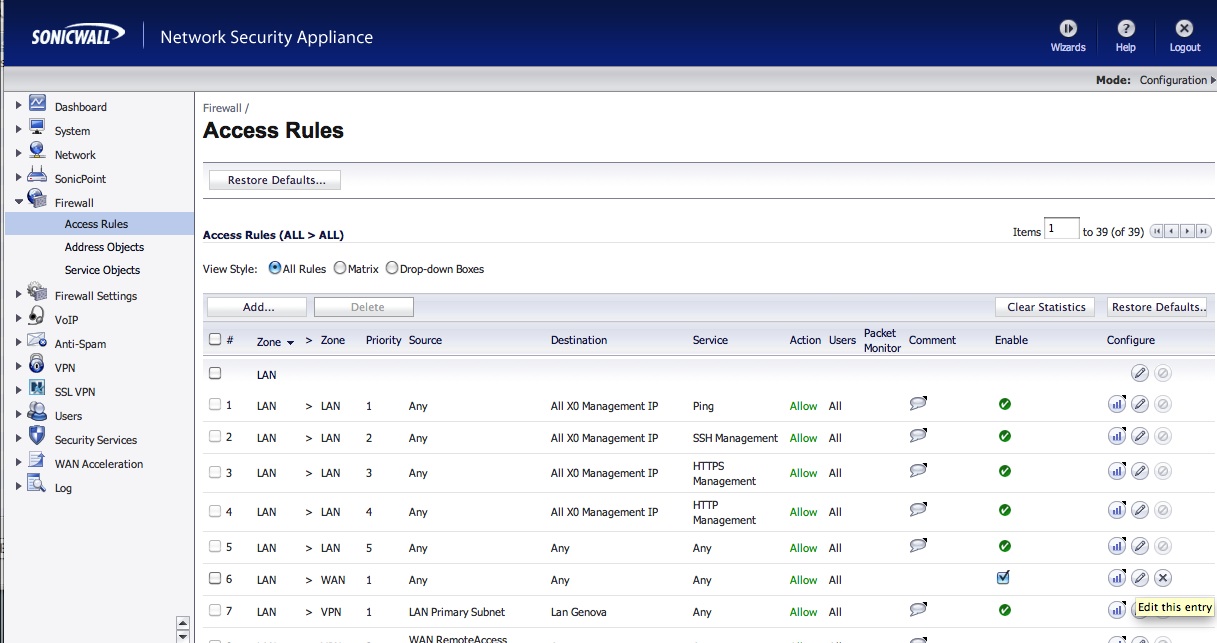
Att.: All the UDP connection related to outbound traffic will be treated by the Sonicwall with this value.
Voip –> Settings
Check the flag “Enable Consistent NAT” e uncheck the flag “Enable SIP Transformations”.
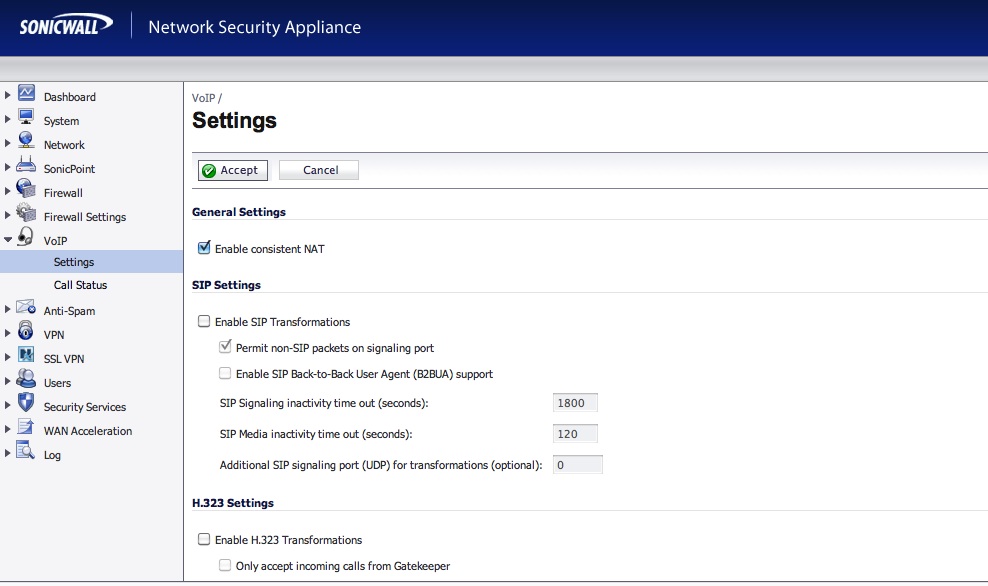 Address translation (NAT) involves rewriting the source port before send the packet in WAN, so that the NAT device can keep track of connections: for reliable two-way communications, the same re-writing must always be used. For example say your internal Asterisk server sends a registration message using source and destination ports of 5060/UDP to your SIP trunk provider’s server on the other side of the NAT device: the NAT software inside Sonicwall will rewrite the source port to some random unused port number, like 14001/UDP. The provider’s server will note your source port, so that it can contact your server if a call comes in (receiving call): if you want to receive calls from the provider, you must ensure that the 14001 port must be associated with the 5060/UDP port on your internal Asterisk server. In Sonicwall to have this behavior you have to set the flag “Enable consistent NAT”.
Address translation (NAT) involves rewriting the source port before send the packet in WAN, so that the NAT device can keep track of connections: for reliable two-way communications, the same re-writing must always be used. For example say your internal Asterisk server sends a registration message using source and destination ports of 5060/UDP to your SIP trunk provider’s server on the other side of the NAT device: the NAT software inside Sonicwall will rewrite the source port to some random unused port number, like 14001/UDP. The provider’s server will note your source port, so that it can contact your server if a call comes in (receiving call): if you want to receive calls from the provider, you must ensure that the 14001 port must be associated with the 5060/UDP port on your internal Asterisk server. In Sonicwall to have this behavior you have to set the flag “Enable consistent NAT”.
The protocol used from Asterisk in SIP is UDP, that is connectionless, so the connection between the two ports (5060-14001) will be kept a certain time, because it is not no way to know if the connection is terminated or not. For this reason the associations will be will be maintained until a timeout: the default in Soniwall in 30s, less than the Asterisk default SIP registration refresh period of 60 seconds! We had increased this value more than the registration refresh period: we increase safety this value to 90s.
Att.: It is possible to change the Asterisk registration refresh period too, but I prefer this solution (change the configuration of Sonicwall): in old Asterisk version the minimum value is 60s.
All these changes are sufficient more often than not: for the unfortunate cases, then you need to directly forwards all the ports used by the SIP flow communication directly from WAN to the PBX.
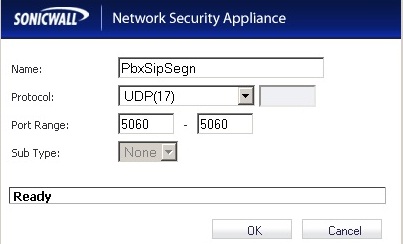
In the next we will redirect all the all the necessary ports to the PBX (5060/UDP and the range from 10000/UDP to 20000/UDP).
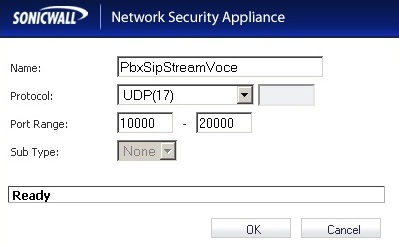
Firewall -> Service Objects
Create two new Custom Service Objects: PbxSipSegn & PbxSipStreamVoce.
 Create one new Custom Service Group, and link the 2 Service Objects created before.
Create one new Custom Service Group, and link the 2 Service Objects created before.
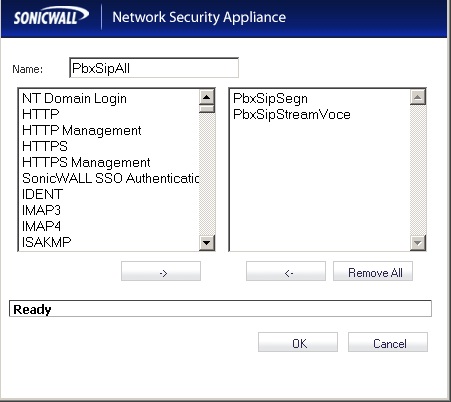
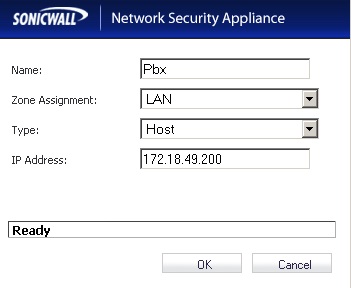
Firewall -> Address Objects
Create one new Custom Address Objects using the LAN IP of the PBX (in my case 172.18.49.200).
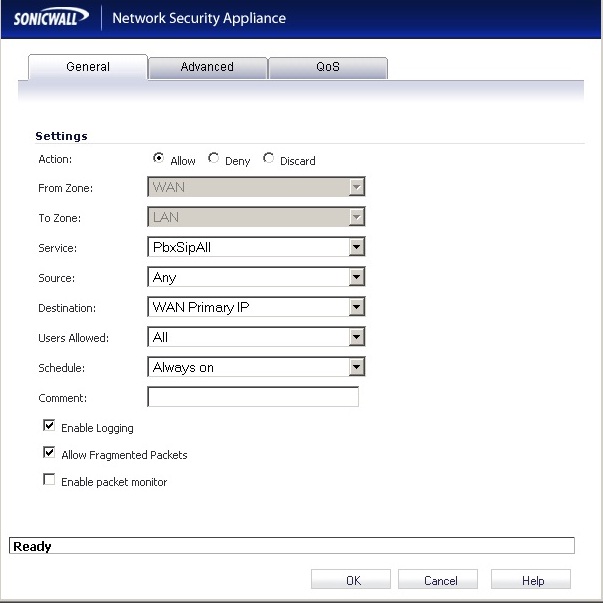
Firewall -> Address Rules
After creating the necessary objects now let’s change the firewall rules: add a new rule WAN->LAN.
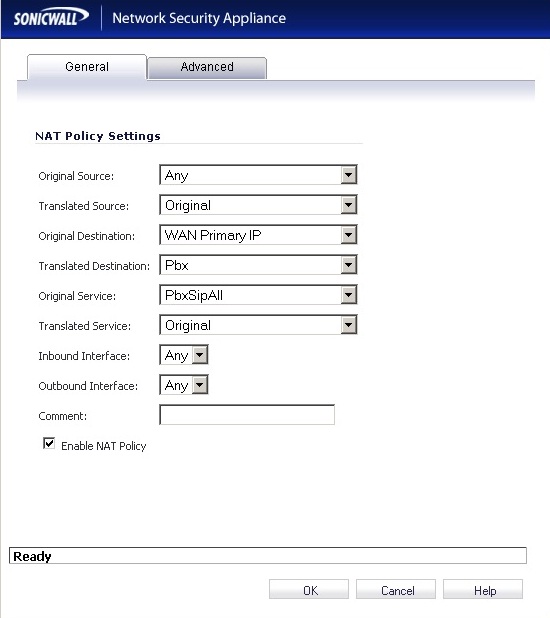
Network -> NAT Policies
The last step: we have to create the NAT policy
Obviously you must also change the parameters in Asterisk: you must edit the sip_nat.conf file.
Externip = <External ip address> localnet = <Network address of the LAN network/Subnet Mask>
In the trunk conf you must add the next parameter.
nat = yes

 Follow
Follow