 This post is just focused on building a vpn IPSec connection site-to-site between IpCop and PFSense.
This post is just focused on building a vpn IPSec connection site-to-site between IpCop and PFSense.
Att: PfSense and IpCop boxes are using a public ip address on WAN side.
PFSense Configuration
– Go under VPN menu, option IPSec, and check Enable IPSec check box, and hit Save button. Then click the Add tunnel icon on the right side of the page, now you’ve a new page where you can specify VPN tunnel options.
– Mandatory Parameters
Uncheck Disabled
Key Exchange Version: V1
Internet Protocol: IpV4
Interface: WAN
Remote Gateway: The public ip address of IpCop box
Phase 1 proposal (Authentication)
Authentication method: Mutual PSK
Authentication method: Main
My identifier: My Ip Address
Peer identifier: Peer ip address
Pre-Shared Key: VERY STRONG PASSWORD
Phase 1 proposal (Algorithms)
Encryption algorithm: Blowfish (256 bits)
Hash algorithm: SHA1
DH key group: 5 (1536 bits)
Lifetime: 28800
– Hit Save button and then click on “Add phase 2”
– Mandatory Parameters
Local Network: LAN Subnet
Remote Network: LANSubnet on ipcop side
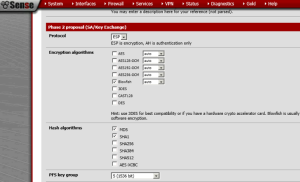
Phase 2 proposal (SA/Key Exchange)
Protocol: ESP
Encryption algorithms: check only on BlowFish (Auto)
Hash algorithms: check only on SHA1 and MD5
PFS key group: 5 (1536 bits)
Lifetime: 28800
 – Hit Save button
– Hit Save button
IpCop Configuration
– On VPNs menu, modify the Public IP with the real WAN ip address
– Press Add button in the middle of the screen to create a new PSK VPN connection with IPSec, then select Net-to-Net Virtual Private Network to continue.
– Mandatory Parameters
Host IP Address: Wan Ip Address
Remote Host/IP: The public ip address of PfSense box
Local Subnet: Local LAN subnet
Remote Subnet: LAN subnet on PfSense side.
Check USe Pre-Shared Key and add the same very strong password used in pfSense
– Hit Save button and then click on Edit advanced settings
– Mandatory Parameters
Phase 1
IKE Encryption: Blowfish (both 256bit and 128bit)
IKE Integrity: check SHA and MD5
IKE Grouptype: set MODP-1536
IKE Lifetime: 1 hour
Phase 2
ESP Encryption: Blowfish (both 256bit and 128bit)
ESP Integrity: check SHA1 and MD5
ESP Grouptype: set to MODP-1536
ESP Keylife: set to 8 hours
Check only Perfect Forward Secrecy (PFS)
– Hit Save button
On PFSense side you need to go to Status menu, IPSec option and in the Overview tab you’ll see the vpn status. If all works fine you have to modify the PfSense firewall.
Firewall -> Rules -> IpSec.
And now PfSense and IpCop are really great friends !
Linkografia
https://www.linux.com/community/blogs/129-servers/398482

 Follow
Follow