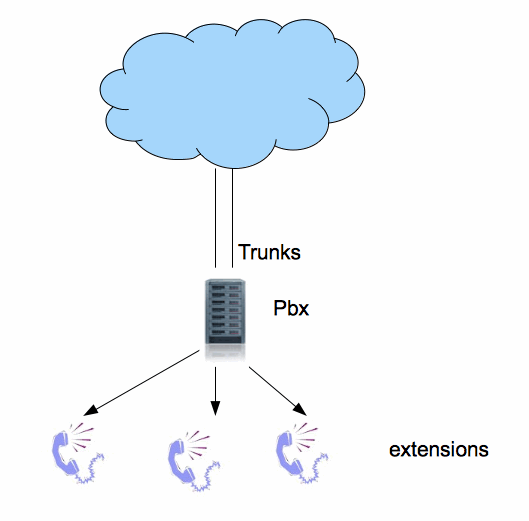
Definition of Trunks
Trunk lines are the phone lines coming into the PBX from the telephone provider. Trunking saves cost, because there are usually fewer trunk lines than extension lines, since it is unusual in most offices to have all extension lines in use for external calls at once.
Att.: Definition partially taken from Wikipedia (http://en.wikipedia.org/wiki/Trunking)
Att.: Normally it is possible to use the ratio 1:5 for trunks:extensions.
Similarly a Sip Trunk is a service offered by an ITSP (Internet Telephony Service Provider) that permits businesses that have a PBX installed to call outside the enterprise network to all phone in the public network (SIP or not) by using the same connection as the Internet connection, .
In the other words if Bob, that use a SIP Pbx, want to call Ada, and Ada’s phone is an old-fashioned analog phone, the Bob’s Pbx must use a trunk line and a service offered by an ITSP.
NAT & SIP
It is impossible tell about SIP & SDP/RTP without mentioning problems related to NAT and the problems it can introduce.
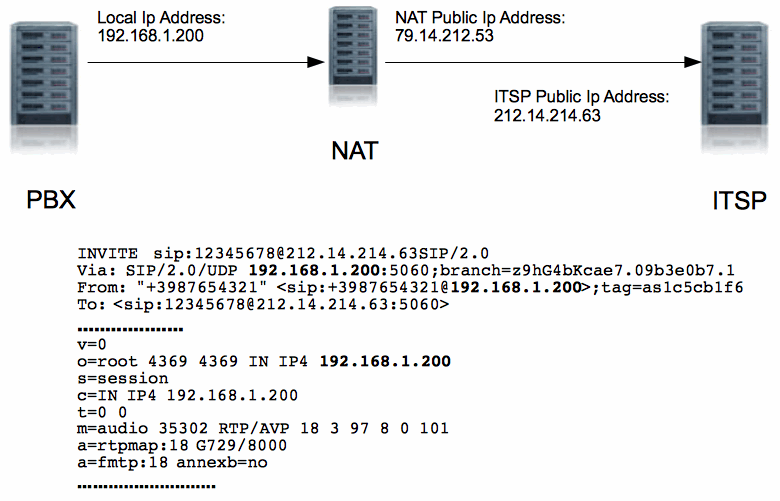
Att.: If the pbx, phone, and other related devices are all in the same LAN, the NAT it is not involved, and it is possible to not know anything about these problems. But very often the pbx use a trunk that is connected to ITSP, and the connection very often traverse a NAT device: in this case the NAT interfere with this process.
NAT (Network Address Translation or Network Address Translator) is the process of translation of an Internet Protocol address (IP address) used within one network (i.e. internal LAN) to a different IP address known within another network (i.e. WAN, that is the “external network”). Typically, an office maps its local inside network addresses that accesses to internet to one or more global outside IP addresses and unmaps the global IP addresses on incoming packets back into local IP addresses. NAT conserves on the number of global IP addresses that a company needs to connects to internet, and it lets the company use up to a single IP address: this address is often used by the router that connects the computers to the Internet.
The simplest type of NAT provides a one to one translation of IP addresses (basic NAT or one-to-one NAT). In this type of NAT only the IP addresses, IP header checksum and any higher level checksums that include the IP address need to be changed. The rest of the packet can be left untouched (at least for basic TCP/UDP functionality, some higher level protocols may need further translation). Basic NATs can be used when there is a requirement to interconnect two IP networks with incompatible addressing.
However it is common to hide an entire IP address space, usually consisting of private IP addresses, behind a single IP address (or in some cases a small group of IP addresses) in another (usually public) address space. To avoid ambiguity in the handling of returned packets, a one-to-many NAT must alter higher level information such as TCP/UDP ports in outgoing communications and must maintain a translation table so that return packets can be correctly translated back. The term for this kind of NAT are NAPT (network address and port translation), PAT (port address translation), IP masquerading, NAT Overload and many-to-one NAT.
Att.: Since this is the most common type of NAT it is often referred to simply as NAT.
As described, the method enables communication through the router only when the conversation originates in the masqueraded network, since this establishes the translation tables. For example, a web browser in the masqueraded network can browse a website outside, but a web browser outside could not browse a web site in the masqueraded network. However, most NAT devices today allow the network administrator to configure translation table entries for permanent use. This feature is often referred to as “static NAT” or port forwarding and allows traffic originating in the “outside” network to reach designated hosts in the masqueraded network.
We have to tell that SIP & SDP/RTP are good protocols, but things kind of break down when NAT gets involved. SIP packets themselves tend to move about without too much trouble (generally), as they ‘hop’ from one server to another: RTP sessions (voice transport) are somewhat more troublesome. The reason is that the NAT modify the port and the address of the Ip protocols, left unchanged the SDP/RTP packets, and it lead to inconsistent message between devices.
Either both clients need to be aware they are behind a NAT, and substitute their local IP addresses for their public IPs in their Session Description messages (the messages that specify the ip address/port to use to transmit voice stream) and open the appropriate firewall ports, or something has to modify the SIP packets en route.
Alternatively it is possible to use NAT device that are equipped with SIP proxy (i.e. siproxd) that intercept all the SIP/SDP/RTP packet and check the used Ip address, substitute the wrong value and retransmit the packet and “open the port” in the NAT for the incoming streaming audio.
Att: Very often if the SIP UA does not modify the Ip address in SIP/SDP message, and the NAT device is not using a Sip proxy, and all works fine too: it depends on the kind of the NAT that the LAN is in using, and if the receiver of the SIP/SDP message is capable of handle message with private local Ip address in SIP/SDP message.
Products known as Back-to-Back User Agents (i.e. Asterisk), can actually proxy RTP traffic: Asterisk can modify SIP packets to direct the caller and destination to establish an RTP session with itself, rather than with each other. This is useful in situations where two SIP clients may not have direct access to each other, most commonly, when one or both of the SIP clients are behind a NAT.
The argument SIP & NAT is very difficult, and to truly understand something to be studied in depth and much documentation. In general, to avoid any problem when possible is always best to use the pbx with a public IP address to connect to ITSP, but this leads to problems relating to safety.
Otherwise in the next some advice.
– Configure the pbx to substitute their local IP addresses for their public IPs in their Session Description messages and related messages
– Configure the pbx to transmit periodically an OPTION packet to the ITSP
– If you have differente devices that connect to external ITSP using SIP you have to modify the originating port used by the protocol: every devices must use a unique different port.
– If you can configure router create static NAT to forward to the pbx all the ports used by the SIP protocol & RDP stream.
PREVIOUS POST: From Sip to RTP (Part 4) – Invite & Register friendship
NEXT POST: From SIP to RTP (Part 6) – The phone is ringing….
Linkografia
http://www.techterms.com/definition/nat
http://en.wikipedia.org/wiki/Network_address_translation

 Follow
Follow